The Ignyte Assurance Platform offers compliance-sensitive teams, such as government contractors, cloud service providers, and healthcare organizations with start-to-finish support as they align with the frameworks they need – all in one platform, backed by personalized consulting and audit services.

Conducting manual IT asset collection and network discovery is time-consuming and costly. And even when an organization achieves compliance, these processes are difficult to maintain and scale to other frameworks.
Compliance isn’t one-size-fits-all. Businesses and organizations of all sizes need an assurance partner that will understand their unique needs.
Identify cyber risk and security gaps across all of your security and technology vendors, and pull them all into one dashboard for your team and auditors to view and act on.
Every day your organization is out of compliance leaves revenue on the table. Automate manual processes and restore client confidence, so you can focus on strategic work.
Our automated GRC platform and a team of former US Department of Defense assessors and security managers is ready to help you achieve compliance, maintain near real-time transparency, and proactively prepare for compliance audits.
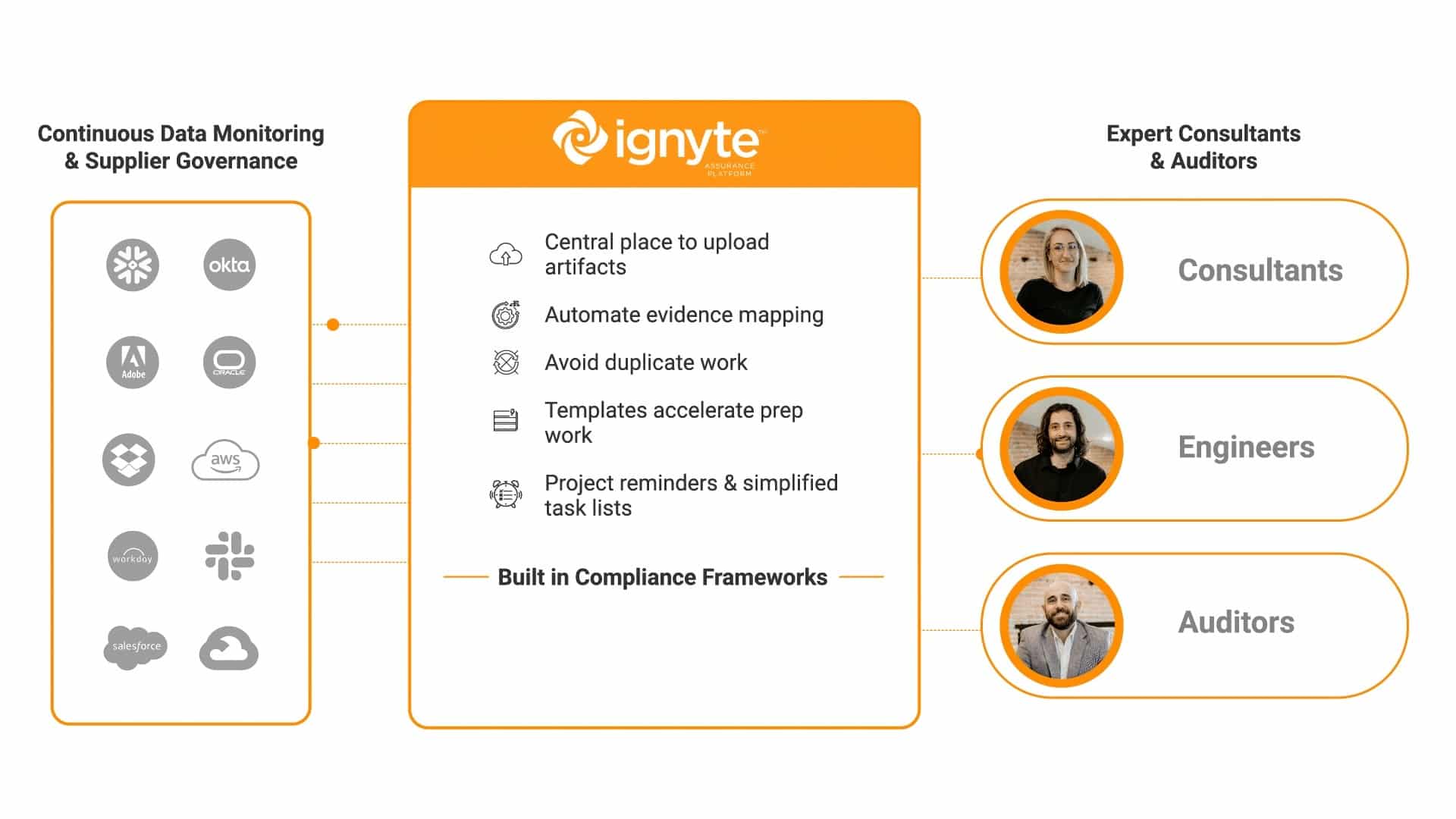
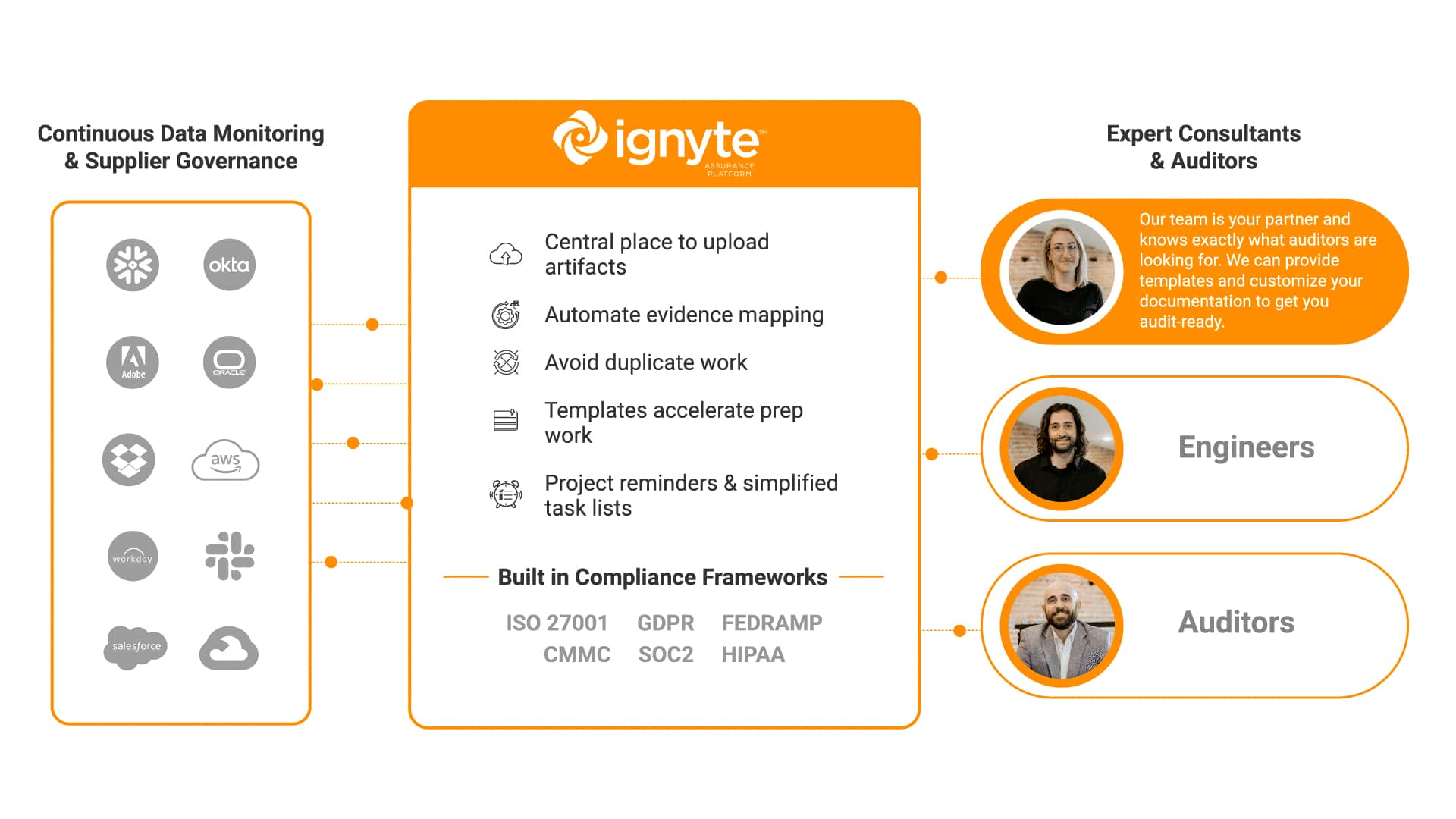

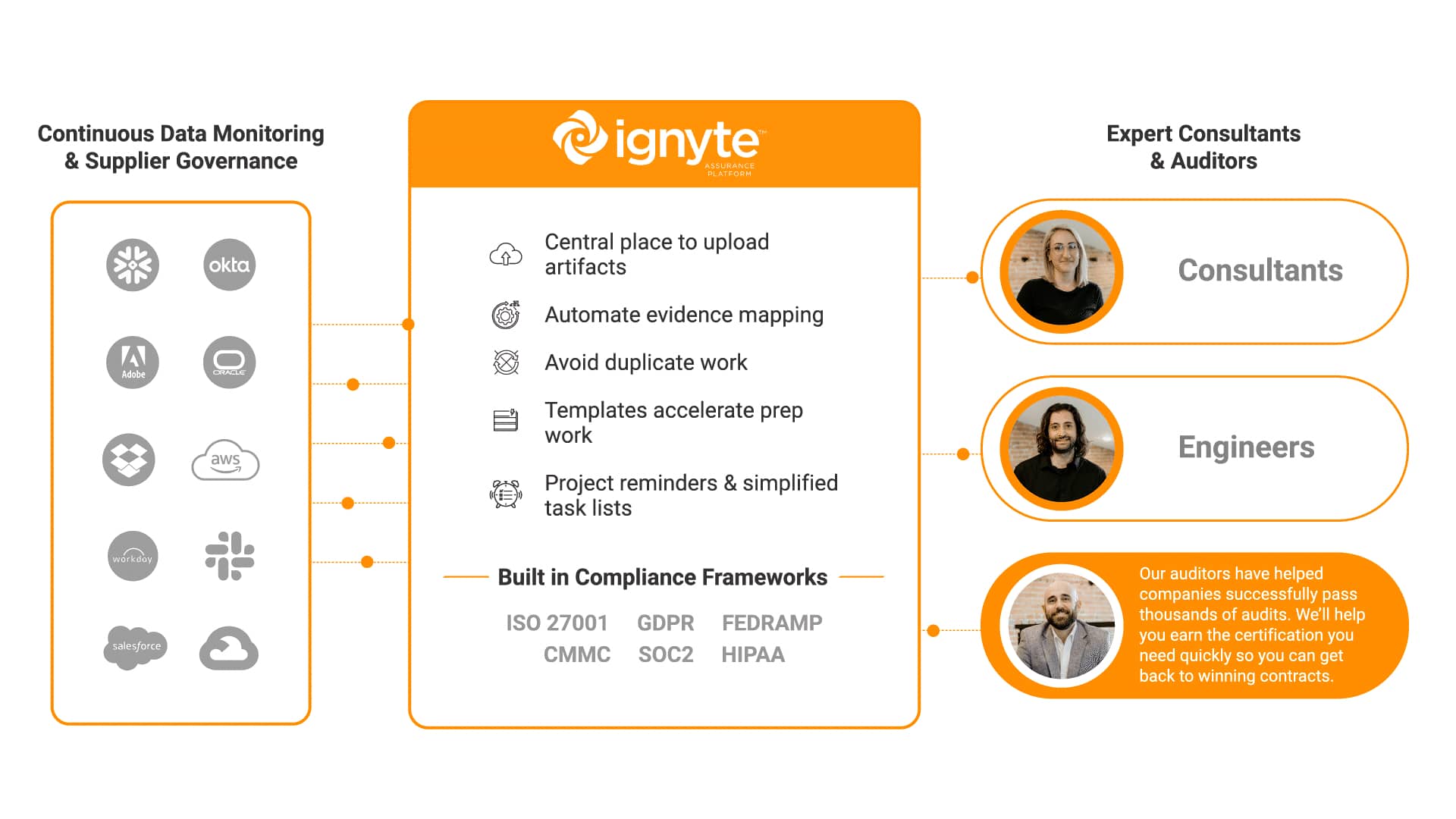
Ignyte’s team of consultants are prepared to help you rapidly achieve certification for major compliance frameworks, including CMMC, FedRAMP, ISO 27001, and more.

Ignyte customers can create and access customizable dashboards, cross-mapping frameworks, and automatically generate near real-time compliance reports.

Ignyte has helped customers move ten times faster during a compliance audit process.

Ignyte’s platform and services will meet you where your compliance program is.
Ignyte’s team of consultants are prepared to help you rapidly achieve certification for major compliance frameworks, including CMMC, FedRAMP, ISO 27001, and more.
Ignyte customers can create and access customizable dashboards, cross-mapping frameworks, and automatically generate near real-time compliance reports.
Ignyte has helped customers move ten times faster during a compliance audit process.
Conducting manual IT asset collection and network discovery is time-consuming and costly. And even when an organization achieves compliance, these processes are difficult to maintain and scale to other frameworks.
See how Ignyte’s consulting services have helped contractors serving the Defense Industrial Base prepare for CMMC enforcement in 2025.
Streamline long authorization processes with cost-effective automations, rapid reporting, and comprehensive audit dashboards.
Ignyte empowers healthcare providers to establish and maintain trust with their patients.









Conducting manual IT asset collection and network discovery is time-consuming and costly. And even when an organization achieves compliance, these processes are difficult to maintain and scale to other frameworks.